Introduction :
As probably seen in several breaking news, during this ever-increasing digital era, cyber-attacks are increasing through different services, applications and any kind of things that are connected and have external interfaces.
In this article, the differences between two macro cases are generally discussed; Cybersecurity in IT (Information Technology) environments and cybersecurity in OT(Operational Technology) environments.
Afterward, it is discussed about the lack of awareness in OT environments about cybersecurity matters. This concept could be so crucial in most of the corporates that invest in cybersecurity activities without a clear distinction between IT and OT ambient.
IT security :
Information Technology(IT) security refers to the data saved in databases like SQL, Cloud data, and in brief speaking all the data stored on servers of the company which are used for different purposes like marketing, CRM and analysis. The data collected and stored in this field are produced from web/desktop applications or user interactions.
The protocols which are necessary to know in this field are at least ( not limited to) HTTP(S), TCP/IP, SNMP, DNS, FTP, SSL, TLS, etc.
Most of the technologies which are used in this area are some hardware and software that are COTS (Commercial Off The Shelf) with the application view and are mostly designed by the dedicated IT department.
From the security point of view, IT security prioritizes more on confidentiality, integrity and then the availability of the systems/data [*].
OT security :
Operational Technology(OT) security tries to protect the security level of the data which are present on PLC, SCADA, and HMI systems. The protocols which are dealt with in OT would be RTU, Ethercat, MODBUS, etc.
Most of the data in this field are collected from sensors. In OT security the safety of the operator and availability of the ICS (Industrial Control Systems) are more important concerning the integrity and confidentiality of the stored data[*].
The OT environments have more relationship with hardware concerning the IT systems.
[*] The priority of CIA (Confidentiality, Integrity, Availability) for each asset and each product should be analyzed precisely. The prioritization level in this article is approximate and indicative which happens in most cases, it cannot be judged for all of the scenarios.
Standards and compliance :
The most well-known standards used in IT environments are ISO 27001. The ISO 27k family discusses best practices and recommendations on information security management similar in design to management systems for quality assurance (the ISO 9000 series), environmental protection (the ISO 14000 series) and other management systems. If you want more information, you can refer simply to the Wikipedia link (https://en.wikipedia.org/wiki/ISO/IEC_27000-series), and see the different parts of ISO 27000.
instead in the OT industry, IEC 62443 is widely used In the following image, the different parts of IEC 62443 are shown.
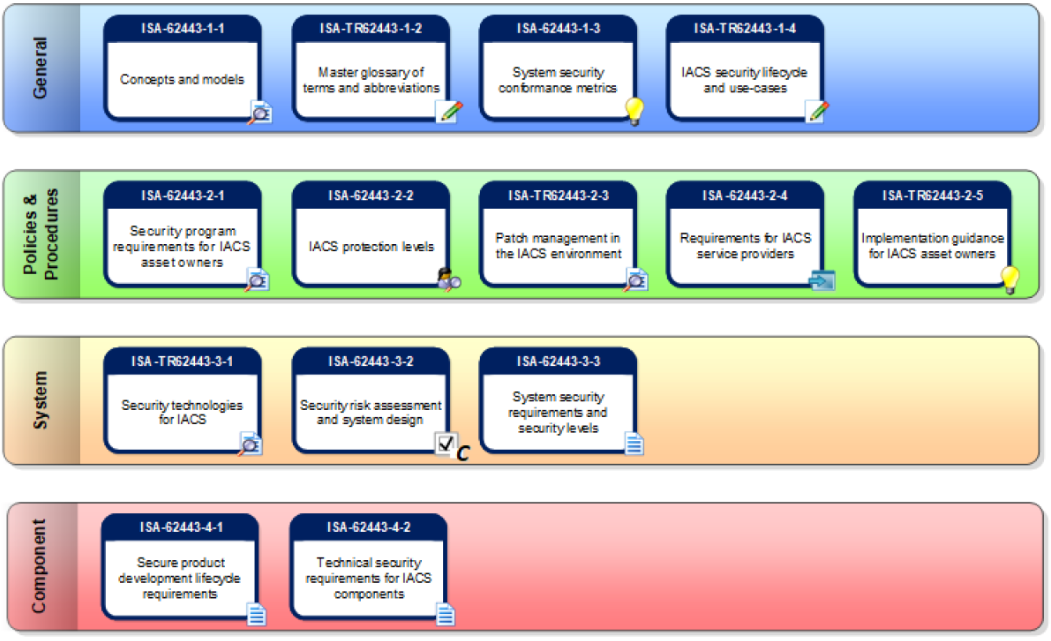
As seen in the image above, there are four macro categories in this standard general, policies and procedures, system level and finally component level.
Different certification bodies certify the companies or products according to the IEC 62443. These types of certifications based on where and how are issued could be defined on different levels like organizational level, system level, and component level.
Attack Techniques :
From an attacker's point of view, different types of proficiencies are needed to exploit the vulnerabilities inside the IT systems and OT systems.
Most of the threats in the OT systems could be malware infection through the external interface of the hardware. For instance, the attacks target Bluetooth interface or ethernet interface or NFC technology. Therefore for protection against these types of attacks, deep knowledge about the abovementioned protocols and interfaces is needed. In addition knowledge about OT threats have a strict relationship with hardware aspects. It means without a great mixture of hardware and software techniques, protection against OT threats is an impossible dream. Let me give an example in the automotive or railway industry where CAN protocol is used. CAN protocol is not a secured-design protocol but it is widely used in some industries for transmission of the data and communication between components. So how a security engineer wants to give mitigation mechanisms for the protection of one component that uses CAN protocol? Can he/she do it without deep knowledge of CAN protocol? Can security engineers help software or hardware engineer without familiarity with the toolchain that is used in the development cycle of the component? The response to these questions is obviously: NO.
On the other hand, as you might know, very well, the OWASP foundation always lists the most common top-found vulnerabilities inside web applications. We can simply refer to them as the most common vulnerabilities inside IT systems. SQL injection, cross-site scripting, and server-side request forgery are some examples of common attack techniques which are used for exploiting eventual vulnerabilities inside the web application and generally inside the IT systems.
If we look more carefully at this concept, in some cases there is very proximity between OT and IT systems. It means that the security experts in these two areas should collaborate for solving the security issues for the whole of the system. Suppose that we have a scenario in which data are collected from PLCs and sensors and then transmitted to the back-end cloud for analysis. In this scenario, the protection mechanisms on PLCs and sensors on the site should be cared for by the OT security experts, but the cloud protection should be handled by the IT security experts. Generally, both two teams should collaborate for the protection of the whole ecosystem.
Awareness in OT :
As we know, IT security has more age concerning OT systems. There are so many well-known techniques and knowledge for the protection of IT systems. As mentioned above there are some foundations and organizations like OWASP which lead the communities toward best practices for IT systems but a comparable scenario does not exist for OT world.
Lack of awareness comes from not knowing the attack techniques which are used by attackers in this field. There is a huge knowledge gap between software/hardware, system engineers who are working in industrial sites and the real cybersecurity world.
It needs so much time for filling this gap. first of all, organizations should be obliged to respect some regulations and processes. We daily hear a lot about cyber attacks on OT systems and it will become more crucial and daunting when these attacks happen against critical infrastructures of one region like energy or water distribution system (visit link below: cyber attack to Florida water supply: https://gca.isa.org/blog/the-florida-water-supply-incident-and-ics-cybersecurity ).
To be honest most of these attacks could simply be prevented only with awareness and training of the personnel but unfortunately, even this simple step has not started in most companies.


