Group Policy is a powerful tool in Windows Server 2019 that allows administrators to define configurations for users and computers within an Active Directory (AD) environment. When properly utilized, Group Policy can help create a more secure and efficient network. This article will guide you through implementing a secure Group Policy in Windows Server 2019 with the Domain Controller role.
Understanding Group Policy
Group Policy is a hierarchical infrastructure that allows a network administrator to implement specific configurations for users and computers. Group Policies are applied to Active Directory Objects like Organizational Units (OUs), domains, and sites. They can manage both user and computer environments using a centralized approach.
Setting Up the Domain Controller
Before you can implement Group Policy, you need a functioning Domain Controller. Once you've installed Windows Server 2019, you can promote it to a domain controller using the Active Directory Domain Services (AD DS) role. Remember, your server should have a strong password policy, and automatic updates should be enabled to ensure that it has the latest security patches.
Creating a Group Policy Object (GPO)
Once your domain controller is set up, you can create a Group Policy Object. In the Server Manager Dashboard, navigate to 'Tools' > 'Group Policy Management'. Expand the forest and domain, right-click on the OU for which you wish to create a GPO, and select 'Create a GPO in this domain, and Link it here'. Name your GPO and click 'OK'.
Implementing Secure Group Policies
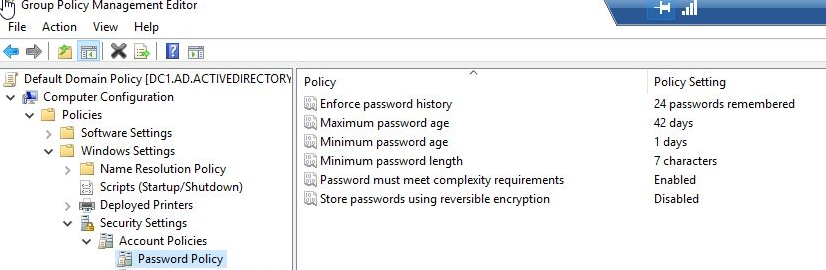
Password Policies: Passwords are often the first line of defense against unauthorized access. Navigate to 'Computer Configuration' > 'Policies' > 'Windows Settings' > 'Security Settings' > 'Account Policies' > 'Password Policy'. Set the policies here, such as 'Minimum password length' and 'Password must meet complexity requirements', according to your organization's security requirements.
Account Lockout Policies: This policy determines the number of failed login attempts that will cause a user account to be locked. You can set this up under 'Account Policies' > 'Account Lockout Policy'. Ensure the policy is stringent enough to prevent brute force attacks but reasonable enough not to lock out users unnecessarily.
User Rights Assignment: Under 'Local Policies' > 'User Rights Assignment', you can control which users or groups have rights to perform certain actions. For instance, you can limit who can shut down the system or log in locally.
Windows Firewall: To protect your network from external threats, ensure Windows Firewall is enabled on all systems. Under 'Computer Configuration' > 'Policies' > 'Windows Settings' > 'Security Settings' > 'Windows Defender Firewall with Advanced Security', you can set up inbound and outbound rules.
Software Restriction Policies: You can limit the applications that can be run on a system by defining software restriction policies under 'Windows Settings' > 'Security Settings' > 'Software Restriction Policies'. This can help prevent the execution of malicious software.
Audit Policies: Auditing allows you to track events on your systems, which can be crucial in identifying suspicious activity. You can set this up under 'Local Policies' > 'Audit Policy'. Consider enabling auditing for events such as account logon events and system events.
User Configuration: User Configuration policies are applied when a user logs onto a computer. They can be used to control many aspects of the user environment, such as desktop settings, control panel access, and software installation permissions.
Enforcing and Testing GPOs
Once you've configured your GPOs, you need to enforce them. Right-click the GPO and select 'Enforced'. The GPO will now be applied to the selected OU. You can also link a GPO to multiple OUs or the entire domain, as needed.
After enforcing the GPOs, it's crucial to test them to ensure they work as expected. Log into a system that falls under the OU where the GPO is applied. You can use the 'gpresult' command-line tool to verify the applied policies. Open Command Prompt as an administrator and type 'gpresult /r' to see the applied Group Policies.
In some cases, you might need to refresh the Group Policy manually. You can do this by running 'gpupdate /force' in the command line. This forces an immediate refresh of Group Policies, rather than waiting for the automatic refresh.
Maintaining and Updating GPOs
It's important to regularly review and update your GPOs to align with changing business needs and security best practices. Regularly check for unused or outdated GPOs and remove or update them as necessary. Implementing a change management process for GPOs can help keep track of changes and ensure they're reviewed before being applied.
Keep in mind that the more GPOs you have, the longer it takes for them to process. Therefore, try to minimize the number of GPOs by consolidating settings where possible. Use Group Policy Modeling and Group Policy Results in the Group Policy Management Console to troubleshoot and optimize GPO processing.
GPO updates can be automatically modified or maintained using several different built-in Windows tools. Here are some that can be used:
Automating Group Policy updates and maintaining them efficiently can be achieved through several methods. While there's no built-in feature to automate GPO updates in Windows Server, PowerShell scripting, combined with task scheduling, can provide automation capabilities. Here are a few steps you can take:
Use PowerShell Scripts: PowerShell is a powerful tool that can be used to manage Group Policies. You can write PowerShell scripts to automate tasks like creating, linking, or modifying GPOs. PowerShell's Group Policy module provides various cmdlets that you can use to perform these tasks.
Scheduled Tasks: You can schedule your PowerShell scripts to run at regular intervals using Windows Task Scheduler. This way, you can automate tasks such as updating GPO settings, refreshing Group Policy, or generating reports.
Active Directory Administrative Center (ADAC): The ADAC in Windows Server 2019 has a feature known as "Dynamic Access Control" which can help in maintaining GPOs. It allows administrators to apply policies based on claims, which are statements about users and devices. This way, you can dynamically adjust GPOs based on changing conditions.
Use Desired State Configuration (DSC): DSC is a management platform in PowerShell that enables you to manage your IT infrastructure with configuration as code. You can use DSC to enforce consistent configurations across your systems, which can simplify Group Policy management.
Leverage Group Policy Preferences (GPP): GPP allows you to configure, deploy, and manage operating system and application settings you'd typically configure through the operating system or application interface. GPP can reduce the number of scripts you need to write and maintain for common tasks.
Implement Change Management: Change management involves tracking changes to your GPOs and reviewing them before they're applied. It's a crucial part of maintaining GPOs, and it can be automated with tools like Advanced Group Policy Management (AGPM), part of the Microsoft Desktop Optimization Pack (MDOP).
Regular Auditing: Regularly audit your GPOs to ensure they're still needed and are functioning correctly. You can use tools like the Group Policy Management Console and PowerShell cmdlets to generate reports on your GPOs.
Third-Party Tools: Several third-party tools can automate and simplify Group Policy management. Tools like ManageEngine's ADManager Plus or NetIQ's Group Policy Administrator can help automate tasks, provide change control, and offer advanced reporting capabilities.
Automating GPO updates and maintenance can help you manage your IT environment more efficiently. However, it's important to regularly review your automated tasks and scripts to ensure they're still meeting your needs and following best practices.
Conclusion
Implementing a secure Group Policy in Windows Server 2019 with the Domain Controller role is a multifaceted process. It involves setting up the Domain Controller, creating GPOs, and configuring them to meet your organization's security needs. While this can be complex, the benefits of a well-configured Group Policy infrastructure are significant, offering enhanced security and more efficient network management. Regular maintenance and updates are essential to keep your Group Policy infrastructure secure and aligned with your business needs. With careful planning and execution, you can leverage Group Policy to create a secure and efficient network environment.


