Red team or blue team? Technical or non-technical? Offensive or defensive? Linux or Windows? How much programming do I need to know? What tools should I use? These are only several questions that anyone starting their cybersecurity career will have. And while they are all valid questions, they fail to present the big picture.
Bottom-up vs. Top-down
A top-down teaching style focuses on providing students a large view of a subject, immersing them in the big picture without explaining the components that make up the subject.
Unlike a top-down teaching approach, which takes a macro view of a subject first, a bottom-up teaching approach begins with the component parts of a subject, and gradually builds up to the whole.
While bottom-up can work with some students, it's easy to get lost in details and go down the rabbit hole. Web attacks -> OWASP Top 10 -> Client-side attacks -> XSS -> Reflected vs. Stored XSS -> Blind Stored XSS -> Blind XSS WAF Bypass techniques...
Spending 6 months studying exclusively about XSS won't get you anywhere in the beginning as there are so many other basic concepts that one should be aware of when starting a cybersecurity career.
Study plans
Study plans are essential for setting up a strong foundation and deciding what are mentee's goals, what are the skills that they want to cultivate, their preferred ways of learning and what motivates them such that they can benefit the most. A study plan ensures that the student understands:
- why a specific topic is important
- what are the risks and mitigations of the attacks
- how components connect with each other
- how to think as an attacker and chain attacks
- how to think as a defender and protect an organization
Chapter 1 - Components of Corporate Infrastructure
- Session 1 - Case study: eCorp Network Diagram - analyze, discuss and understand components of an organization's network diagram
- Servers
- Workstations
- Databases
- Network Protocols
- Active Directory
- Internal Network
- Internet Facing Assets
- Firewalls
- VPNs
- Cloud
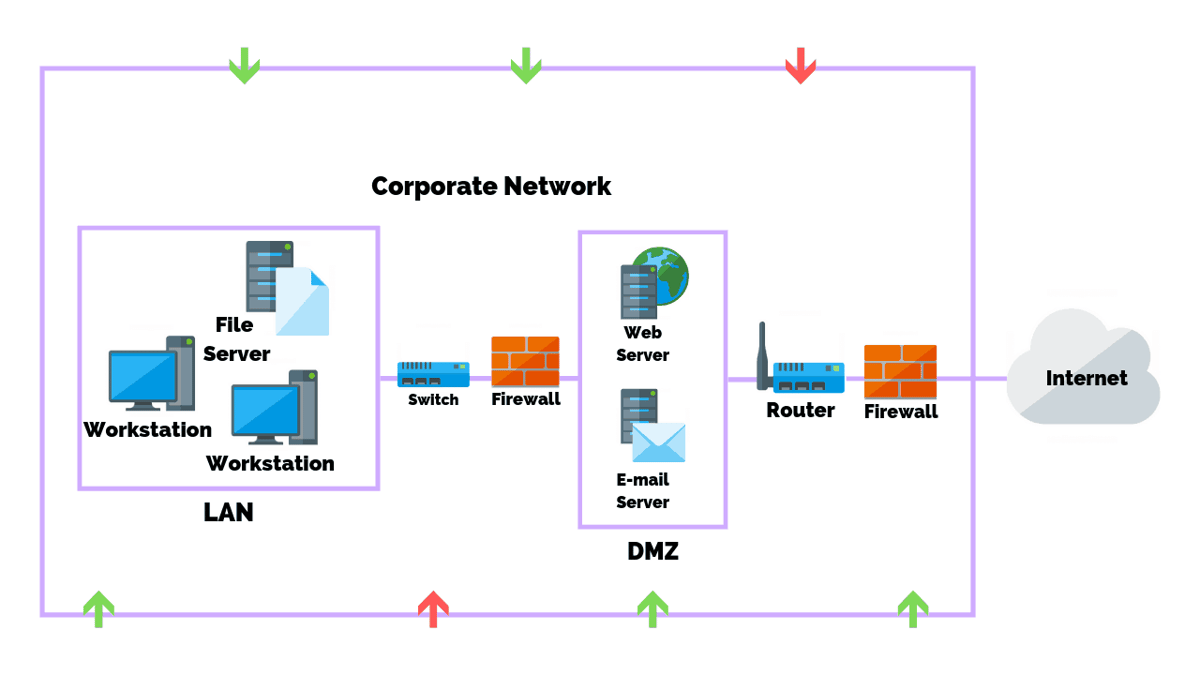
In the following 3 sessions the terminology, key concepts, use cases, roles, interconnection and security risks of each of these components is discussed in depth:
- Session 2: Servers, Workstations, Databases
- Session 3: Internet Facing Assets, Firewalls, VPNs, Cloud
- Session 4: Networking and Active Directory
At the end of this chapter, the mentee should be comfortable to understand most of the network diagrams, understand the terminology, how the components are connected, how they interact with each other, what is their purpose, and where security risks can occur.
Chapter 2 – Attack, Defence, Impact and Mitigation
Once students get more familiar with basic concepts, the next step is to discuss what security risks and defences can be apply at each layer of the organization:
- Session 1 - Servers: port scanning, automate and manual exploitation, information gathering
- Session 2 - Workstations: phishing, social engineering, physical access
- Session 3 - Internet Facing Assets: hacking web applications, mobile applications and APIs
- Session 4 – Firewalls: external/internal firewalls, firewall rules and policies, Web Applications Firewalls (WAF)
- Session 5 – VPNs: privacy, remote work, encryption, breaking external perimeter
- Session 6 – Cloud: on-prem infrastructure vs. cloud, common attacks, defence and risks associated with cloud technology
- Session 7 - Networking: public/private networks, traffic analysis, intrusion detection/protection, log analysis, command and control (C2) communication
- Session 8 - Active Directory: open network shares, kerberoast, password spray (Study case: Conti Ransomware group – leaked manual)
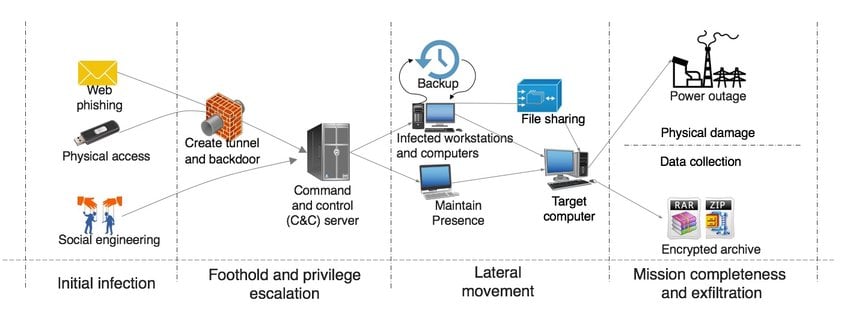
At the end of this chapter, you should have a high level overview of the most common security attacks at each level of a company's infrastructure. You should be able to assess what is the risk of these attacks, how can you protect, mitigate and detect these attacks. The chapter focuses on understanding the main concepts, with limited technical and hand-on exercises.
Chapter 3 – Hand-on Exercises and Practice
The third chapter focuses exclusively on technical skills: setting up a lab, installing tools, performing scanning, attacks and analyzing the logs.

Session 1: scanning, exploitation, information gathering, log analysis
- nmap
- masscan
- exploitdb
- metasploit
- linenum
- linpeas
- seatbelt
Session 2: phishing, social engineering, physical access
- gophish
- evilginx2
- kali bootable usb
Session 3: hacking web applications, mobile applications and APIs
- Burp
- OWASP Top 10
- nikto
- ffuf
- assetfinder
- feroxbuster
Session 4: external/internal firewalls, firewall rules and policies, WAF
- nmap
- iptables
- windows firewall
- wafw00f
- WAF bypasses
Session 5: VPN, SSH tunneling, tor, encryption, opsec
- openvpn
- proxychains
- sshuttle
- chisel
- ngrok
Session 6: Cloud (Azure) - lateral movement and privilege escalation cloud – on prem, ARM and AAD misconfiguration, identity access management
- AzureHound
- StormSpotter
- ROADTools
- MicroBurst
Session 7: traffic analysis, intrusion detection/protection, log analysis, command and control (C2)
- Wireshark
- HELK
- Sysmon
- Suricata
- CobaltStrike
- MITRE ATT&CK
Session 8: Active Directory, open network shares, kerberoast, password spray
- PowerUp
- PowerView
- Rubeus
- DomainPasswordSpray
At the end of this chapter, you should have a deep understanding of common attacks at each level of an organization structure, with hands-on experience. The chapter focuses on practical work and the simulation of these attacks are done against lab machines.
Chapter 4 – Working in the Cybersecurity Industry
While operational work is a key factor for your future job, there are secondary skills required that include:
- Scoping projects
- Documenting findings and report writing
- Result presentation for C-level and technical team
Growing your network
Final words
Preparation before the courses, and homework exercises after each session is expected, as well as taking notes and documenting your research. Each session is expected to take 1-2 weeks both self-study from mentee and guidance from mentor is performed. This study plan is an estimation, and can adjusted based on mentee's knowledge and how they feel about the topics. Once all these is done, it's time to focus on the next steps:
- CV and Job Applications
- Job Interview Preparation
- Specialization and Career Path








