How to become a Cybersecurity Analyst
Becoming a Cybersecurity Analyst is an in-demand career
path. It
requires deep expertise in Cybersecurity and a
strong network to carry you along. Here are some resources to help you on your journey.
Browse
Cybersecurity
experts
Why should you become a
Cybersecurity Analyst?
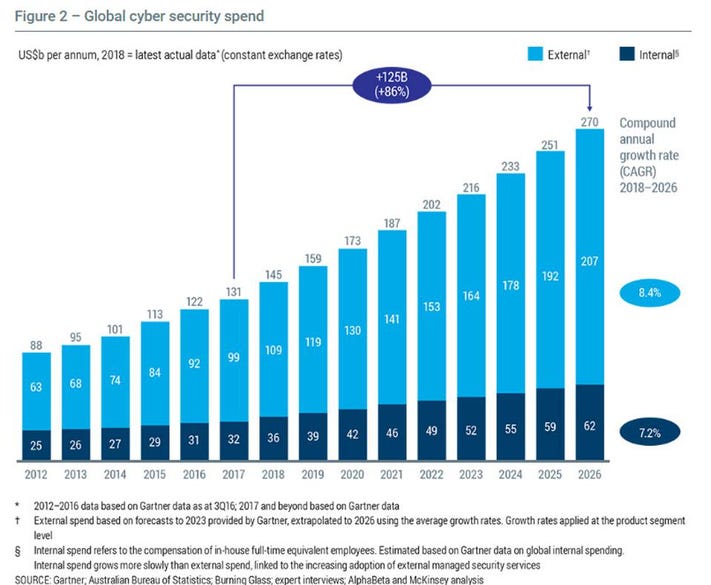
Demand for experts in Cybersecurity is growing rapidly. Companies are
looking for people with deep expertise in the field of Cybersecurity to help
them
build their products and services.
As a result, Cybersecurity Analysts are in high demand and command high salaries. According to leading
sources,
the median salary for a Cybersecurity Analyst is $100,000 and a
senior Cybersecurity Analyst can earn up to $150,000. Even entry-level
positions can command great salaries.
No wonder that interest in a career in Cybersecurity is growing rapidly.
Explore the
resources below to learn more about how to become a Cybersecurity Analyst.
The Cybersecurity must-reads you shouldn't miss.
Key articles and posts of industry experts can help you get a better
picture of what you are getting into.
In our opinion, these are some must-reads you really shouldn't
miss.
How to become a security analyst: A complete career guide
A security analyst is a pretty broad job description that refers to people responsible for monitoring computer infrastructure and information networks to ensure the are protected. The job responsibilities for a security analyst can range from controlling file access and credentialing, to maintaining firewalls and network updates, to proactively trying to hack systems to look for vulnerabilities and weaknesses.
Read more
How to Become a Cyber Security Analyst in 2022
The digital era has made it possible to conduct nearly all personal, professional and financial business online. However, with the benefits of this cyber world also comes the risk of cyber attacks, data breaches and many other online threats. Cyber security analysts play a critical role in preventing cyber attacks or the compromising of systems to protect individuals and large organizations. In this article, we will describe what a cyber security analyst does, why they are important, their average salary, how to become a cyber security analyst and a few frequently asked questions.
Read more
Cybersecurity Analyst Job Description & Role Breakdown
We all know the broad strokes of what cybersecurity professionals do in their day-to-day — they fight cybercrime, patch vulnerabilities, and protect our data. But ask the average layperson to get into the nitty-gritty details of a cybersecurity analyst job description, and they’ll probably draw a blank. While most know that cybersecurity analysts strive to keep people safe online from hackers and scammers, most don’t have a clear idea of what goes into that protection, or of the wide variety of security tasks that cybersecurity professionals execute daily. Unsurprisingly, there’s a lot more to a professional security analyst’s daily task list than the industry’s logline implies. If you’re interested in making a name for yourself in cybersecurity, read on! We’ll explain what you can expect from an entry-level cybersecurity job description, review the qualifications you’ll need to have as a candidate, and address the responsibilities you’ll face when you land your first role.
Read more
What Does a Cybersecurity Analyst Do?
BrainStation’s Cybersecurity Analyst career guide is intended to help you take the first steps toward a lucrative career in the field. Read on to find out more about what a Cybersecurity Analyst does.
Read more
A Day in the Life: What Cybersecurity Pros Actually Do
Cyber security analysts help to protect an organisation by employing a range of technologies and processes to prevent, detect and manage cyber threats
Read more
Cybersecurity Analyst Salary Guide: How Much Can You Make?
If you have an interest in cybersecurity, this is good news. There are more cybersecurity positions than there are qualified people to fill them—nearly half a million open jobs in the US alone [1]. Plus, skilled cybersecurity analysts often get well-compensated for their work. Read on to learn about how much you can expect to earn as a cybersecurity analyst, as well as factors that can influence your salary. If you’re interested in starting or advancing your career in this field, we’ll discuss some ways you may be able to boost your earning potentia
Read more